Configure SAML SSO
Read time: 7 minutes
Last edited: Jul 26, 2024
Overview
This topic explains how to configure your LaunchDarkly account for SSO.
If you're a LaunchDarkly administrator or account owner, you can configure LaunchDarkly to use your IdP when account members authenticate.
This topic includes:
- how to configure your IdP and how to configure SAML within LaunchDarkly
- details on user provisioning
- details on the custom attributes available during provisioning
After your configuration is complete, you can enable SSO. If needed, you can also disable SSO or change SSO providers.
Configure your IdP
To set up a LaunchDarkly connection, follow the instructions for your chosen IdP.
We provide support for the following IdP connectors:
You can only use one identity provider per LaunchDarkly account.
You can use other identity providers with LaunchDarkly, but we do not provide support or configuration guidance for other providers. To learn more, read Supported external identity providers.
Configure LaunchDarkly SAML
To configure SAML within LaunchDarkly:
- Log in to LaunchDarkly as an Owner or Admin.
- Click the gear icon in the left sidenav to view Organization settings.
- Click Security and scroll to the "SSO management" section:
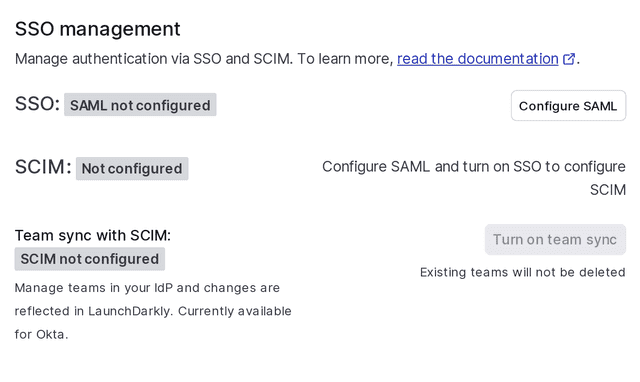
- Click Configure SAML. The SAML configuration panel appears, pre-populated with information you need to set up LaunchDarkly as a SAML application with your identity provider:
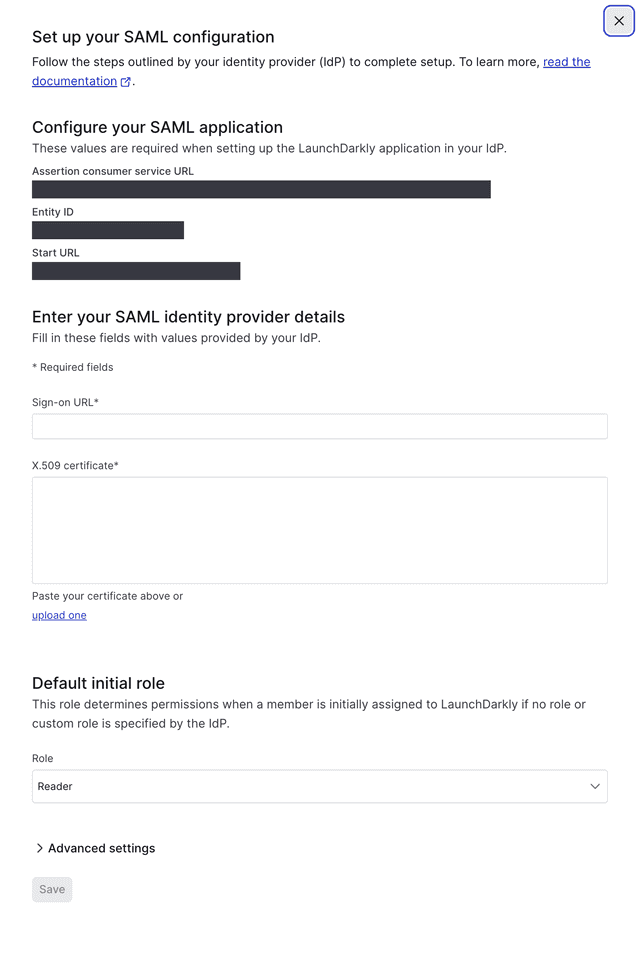
To complete SAML configuration, follow the instructions specific to your IdP. The list of IdPs we support is in the Overview.
Specific configuration details vary between IdPs, but the basic process is the same regardless of which IdP you use.
To configure LaunchDarkly with an external IdP:
- Create the SAML application in your IdP. To do this, follow the instructions in the documentation for your IdP.
- Copy the SAML configuration metadata from the IdP into LaunchDarkly's SAML configuration panel.
- Click Save.
Encrypt SAML assertions
If you choose to encrypt SAML assertions, LaunchDarkly uses a private/public key pair for encryption and provides the public key as an X.509 certificate. You can copy this, upload it into your IdP, and configure your IdP to encrypt SAML assertions.
To encrypt SAML assertions sent by your IdP:
- Click the gear icon in the left sidenav to view Organization settings.
- Click Security and scroll to the "SSO management" section.
- Click Configure SAML. The SAML configuration panel appears.
- Click Advanced settings.
- Check the Enable encrypted SAML assertions checkbox.
- LaunchDarkly uses a public/private key pair for encryption and provides the public key as an X.509 certificate. Click the copy icon to copy the certificate contents. You'll need to upload this into your IdP and configure your IdP to encrypt SAML assertions.
- When the existing certificate is close to expiring, LaunchDarkly provides a new one. Select the newer certificate and copy its contents.
- Click Save.
Manage expired SAML certificates
If your SAML certificate expires, you may not be able to log in to your LaunchDarkly account through SSO. If this happens, start a Support ticket.
We will disable SSO for your account, allowing you to log in with your original email and password. If you have only ever logged in through SSO, you can use the "Forgot your password?" link to log in. To learn how, read Resetting your password.
You can then update your SAML certificate and re-enable SSO.
Test-drive mode
When LaunchDarkly receives a valid SAML configuration, SSO enters test-drive mode. Test-drive mode lets you test the SSO integration before deploying the change to the rest of your organization.
When SSO is in test-drive mode, you can test authentication through your IdP, but LaunchDarkly's login screen will continue to use regular password-based authentication.
To use SSO in test-drive mode:
- Log into LaunchDarkly as an Owner or Admin.
- Click the gear icon in the left sidenav to view Organization settings.
- Click Security and scroll to the "SSO management" section.
- Click Test-drive SSO. This performs the same authentication request flow that occurs for LaunchDarkly-initiated SSO logins:
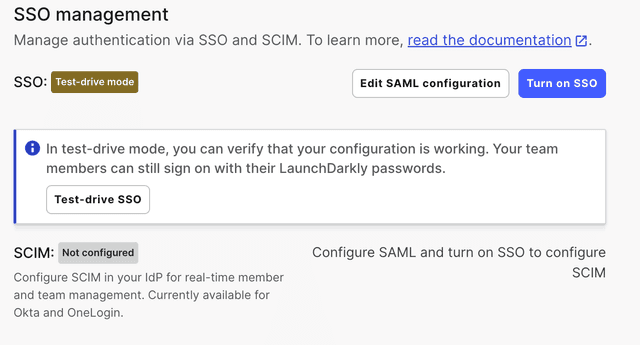
If you need to make changes to your setup, you can edit your SAML configuration while in test-drive mode.
After your configuration is working as expected, you can set up user provisioning and enable SSO for your organization. You will automatically exit test-drive mode when you enable SSO.
To exit test-drive mode and keep SSO disabled, delete the SAML configuration metadata from the SAML configuration panel.
User provisioning with SAML
New account members will not be able to sign in from LaunchDarkly's login screen until they have accessed LaunchDarkly through your IdP at least once. To learn how, read Initiating login through your IdP.
LaunchDarkly automatically creates accounts for new account members who sign in through your IdP. Every time an account member signs in, LaunchDarkly also updates the account member's profile with user attributes from the IdP. To learn more, read Default initial role.
You can configure your identity provider to send the following attributes when the account member signs in to LaunchDarkly. Each attribute is optional. Specify attribute names with the "basic" format. You can also manage custom attributes in LaunchDarkly.
NameID field formatting
LaunchDarkly only supports the use of email addresses in the NameID field. Do not use other types of identifying strings.
Below is an example of an SSO-provided nameID that LaunchDarkly will accept:
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">admin@test.com</saml:NameID>
Set custom attributes
These attributes are available for SAML SSO provisioning and SCIM provisioning:
| Attribute name | Attribute format | Availability | Description |
|---|---|---|---|
| role | string | SSO and SCIM | One of the built-in LaunchDarkly roles: |
| customRole | String array, or comma-separated string | SSO and SCIM | A list of the keys of the custom roles to assign to the account member. These replace the member's existing custom roles. If a member has any custom roles, they supersede the built-in role. The elements of the |
| teamKey | String array, or comma-separated string | SSO only | A list of the keys of the teams that the account member belongs to. These replace the member's existing teams. The elements of the |
SAML SSO supports the following naming attributes:
firstNamelastName
SCIM provisioning uses the standard naming attributes:
givenNamefamilyName