Entra ID (formerly Azure AD)
Read time: 7 minutes
Last edited: Jan 07, 2025
Overview
This topic explains how to integrate LaunchDarkly with Microsoft Entra ID (formerly Azure AD).
The Entra ID App Gallery includes LaunchDarkly and provides a LaunchDarkly application template that facilitates configuration.
Integrate LaunchDarkly with Entra ID
To integrate LaunchDarkly with Entra ID:
- Log in to Entra ID.
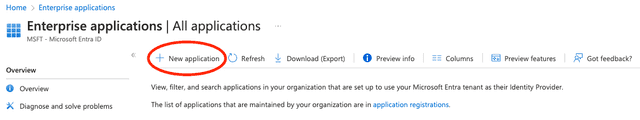
- Navigate to "Enterprise applications."
- Click New application:
- Search for the LaunchDarkly application.
- After you add it, follow the Microsoft Entra integration with LaunchDarkly tutorial.
If your instance of Entra ID manages multiple LaunchDarkly accounts, start a Support ticket.
During configuration, we recommend using the identifier user.mail, provided that every user has their email address attribute set. If you haven't set attributes for every user, use the identifier user.userprincipalname.
If members cannot log in after you set up SSO, read the troubleshooting article New users are unable to log in with Azure AD once SSO is configured.
Map custom roles to Entra User Attributes
After you integrate LaunchDarkly with Entra ID, you can map LaunchDarkly role and custom role attributes to Entra User Attributes using Entra claims. The LaunchDarkly Entra SSO integration provides Just-In-Time (JIT) user provisioning for IdP-Initiated SSO.
To learn more about SSO provisioning for roles and custom roles, read Custom roles.
To set up role and customRole claims in Entra ID:
- Navigate to the "Attributes & Claims" section.
- Click Edit.
- Click Add new claim. The "Manage claim" screen appears:
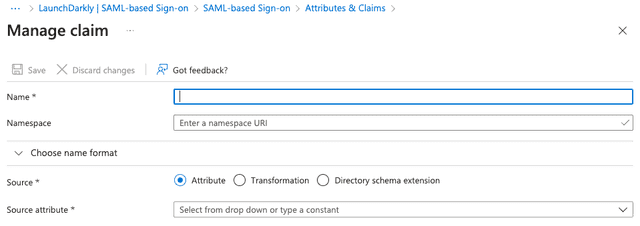
- Enter "role" in the Name field.
- Leave the source as "Attribute."
- Choose a source attribute from the menu that is not currently mapped, such as
user.country. - Click Save:
- Repeat steps 1-7 with "customRole," mapping to a different unused source attribute.
SAML ignores empty fields if used in Roles or customRoles. To clear all existing roles, enter an empty string "" into the field.
Map custom roles to Entra Security Groups
In addition to Entra User Attributes, you can also assign LaunchDarkly custom roles to Entra Security Groups.
There are five steps to this process:
- Create custom roles in LaunchDarkly
- Create groups in Entra ID
- Create roles for the Entra LaunchDarkly Enterprise Application
- Set up groups and roles in the Entra LaunchDarkly Enterprise Application
- Update the Entra LaunchDarkly Enterprise Application SSO configuration
Each of these steps are outlined below.
Create custom roles in LaunchDarkly
To begin, create the custom roles in LaunchDarkly that you want to use with the Entra LaunchDarkly Enterprise Application. Make note of each custom role's key, as you will need the key when you set up your Entra ID app role.
To learn how, read Custom roles.
Create groups in Entra ID
After you have created your custom roles in LaunchDarkly, set up your groups in Entra ID:
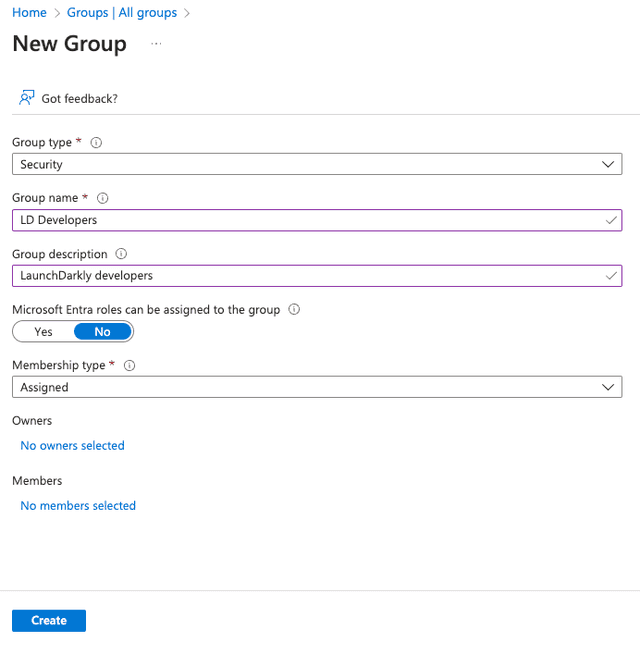
- In Entra ID, navigate to "Groups," then click New group.
- Select a group type and enter a group name.
- Click “No members selected" to add new members:
- Select members from the list to add to the group, then click Select:
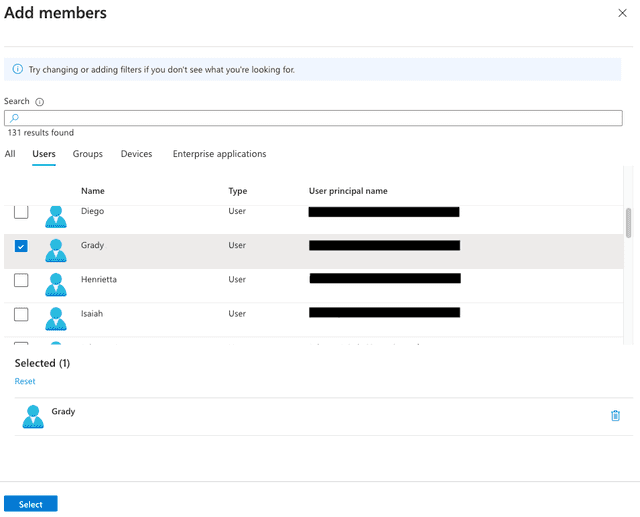
Your Entra ID members are now in the group.
Create roles for the Entra LaunchDarkly Enterprise Application
Next, create roles within Entra ID:
- In Entra ID, open the LaunchDarkly Enterprise Application.
- Navigate to App Registrations, then click All applications:
- Click LaunchDarkly to open the application.
- Navigate to "App roles" and click Create app role.
- Enter the role information. The value must be the key of the custom role you created during the Create custom roles in LaunchDarkly step:
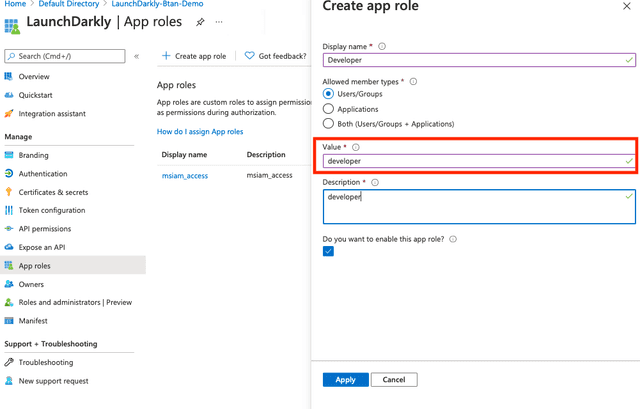
- Click Apply.
Repeat this procedure for each new Entra app role.
Set up groups and roles in the Entra LaunchDarkly Enterprise Application
Then, set up groups and roles in Entra ID:
- In Entra ID, open the LaunchDarkly Enterprise Application.
- Click Users and groups. The "Users and groups" screen appears:
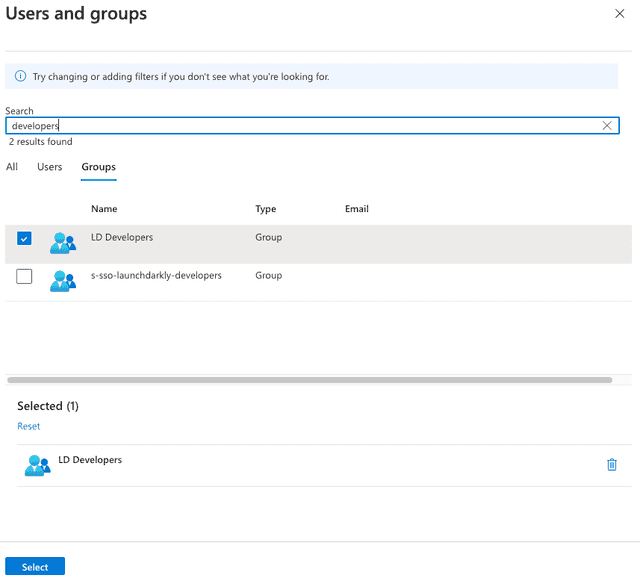
- On the "Groups" tab, choose the group you want to edit and click Select. The "Add Assignment" screen appears.
- Click None Selected under "Users and groups" to add a new group. The "Users and groups" screen appears:
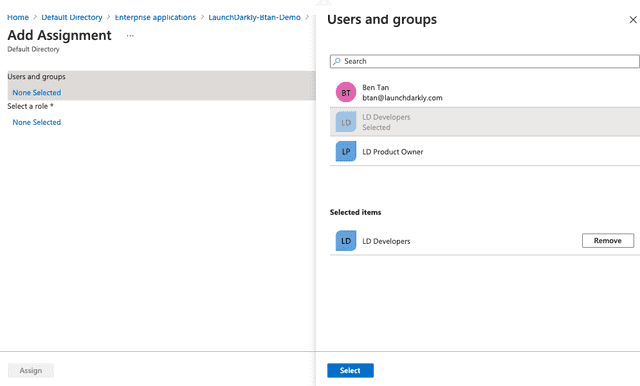
- Choose the group you created in the Create groups in Entra ID step.
- Click Select. You are returned to the "Add Assignment" screen.
- Click None Selected under "Select a new role" to add a new role:
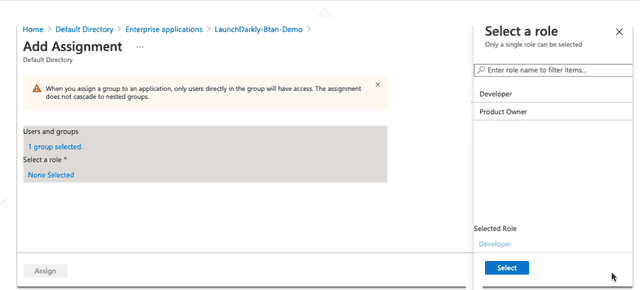
- Choose the role you created in the Create roles for the Entra LaunchDarkly Enterprise Application step.
- Click Select. You are returned to the "Add Assignment" screen.
- Click Assign.
Repeat this procedure for each group and role you want to set up.
Update the Entra LaunchDarkly Enterprise Application SSO configuration
Finally, update Entra's SSO configuration:
- In Entra ID, open the LaunchDarkly Enterprise Application.
- Click Single sign-on.
- Scroll to the "Attributes & Claims" section.
- Click Edit. The "Manage claims" form appears.
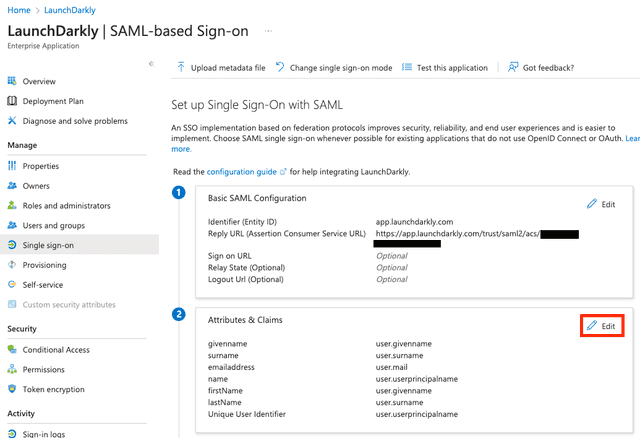
- Enter
customRolein the Name field. - Leave the Namespace field empty.
- Select "Attribute" as the source.
- Enter
user.assignedrolesin the Source attribute field.
- Click Save. You are returned to the "Attributes & Claims" screen.
Close the "Attributes & Claims" screen to return to the "Single sign-on" page. To test your SSO configuration, click Test at the bottom of the page.
For another example of this setup process, read How to setup LaunchDarkly custom roles from Azure AD Security Groups.
Assign Entra ID Security Groups to LaunchDarkly teams
You can assign LaunchDarkly teams to Entra Security Groups. This keeps the members of your LaunchDarkly teams in sync with your Entra ID groups.
There are four steps to this process:
- Create Security Groups in Entra ID
- Create teams in LaunchDarkly
- Assign Entra ID Security Groups to the LaunchDarkly Enterprise Application
- Create a new Entra ID claim
Create Security Groups in Entra ID
First, set up a Security Group in Entra ID:
- In Entra ID, navigate to "Groups," then click New group.
- Select the "Security" group type and enter a group name.
- Click Create. You are returned to the groups list.
- Copy the object ID of the group you want to link to a LaunchDarkly team:
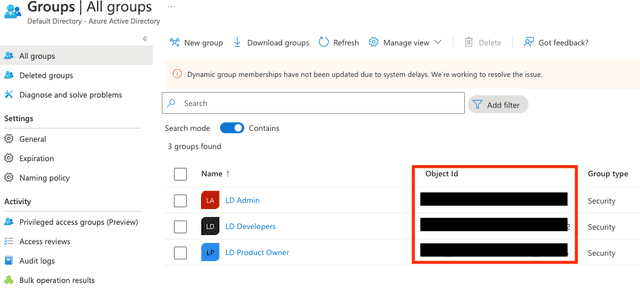
You will use this group's name and ID in the next section.
Repeat this procedure for as many groups you want to assign to LaunchDarkly teams.
Create teams in LaunchDarkly
Next, create a team in LaunchDarkly using your Entra ID Group name and ID:
- Click the gear icon in the left sidenav to view Organization settings.
- Click Teams.
- Click Create team. The "Create team" dialog appears.
- In the Name field, enter your Entra ID group name.
- In the Key field, paste the Entra ID group ID you copied the previous section.
- Click Create team.
Repeat this procedure for as many teams as you want to sync with Entra ID Security Groups.
Assign Entra ID Security Groups to the LaunchDarkly Enterprise Application
Then, assign Entra ID Security Groups to the LaunchDarkly Enterprise Application:
- In Entra ID, open the LaunchDarkly Enterprise Application.
- Click Users and groups. The "Users and groups" screen appears:

- On the "Groups" tab, choose the group you want to edit and click Select. The "Add Assignment" screen appears.
- Click None Selected under "Users and groups" to add a new group. The "Users and groups" screen appears.

- Choose the group you created in the Create Security Groups in Entra ID step.
- Click Select. You are returned to the "Add Assignment" screen.
- Click Assign.
Repeat this procedure for each Entra ID Security Group you created.
Create a new Entra ID claim
Finally, create a new Entra ID claim:
- In Entra ID, open the LaunchDarkly Enterprise Application.
- Click Single sign-on.
- Scroll to the "Attributes & Claims" section.
- Click Edit. The "Manage claims" form appears.

- Click "+ Add a group claim." A "Group Claims" dialog appears.
- Select "Groups assigned to the application" under "Which groups associated with the user should be returned in the claim?"
- Select "Group ID" as the source attribute.
- Open the Advanced options section.
- Check the "Customize the name of the group claim" box.
- Enter
teamKeyinto the Name field:
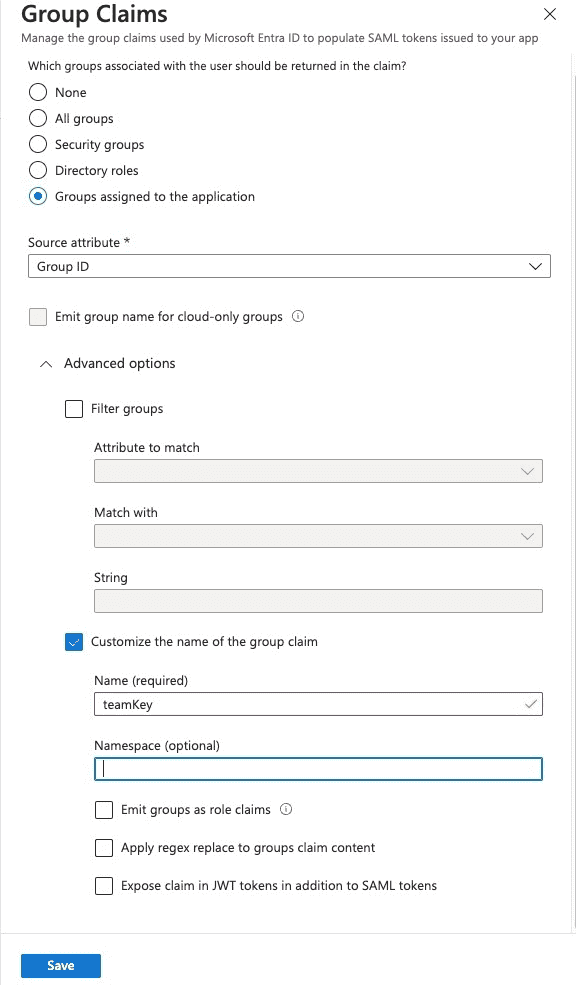
- Click Save. You are returned to the "Attributes & Claims" screen.
Close the "Attributes & Claims" screen to return to the "Single sign-on" page. To test your SSO configuration, click Test at the bottom of the page.