AWS PrivateLink
Read time: 2 minutes
Last edited: Oct 11, 2024
The AWS PrivateLink integration is available to customers on an Enterprise plan. To learn more, read about our pricing. To upgrade your plan, contact Sales.
Overview
This topic explains how to configure and use the PrivateLink integration for LaunchDarkly.
The PrivateLink integration lets you configure AWS PrivateLink to route your event egress traffic through the AWS network backbone. Sending event egress traffic through PrivateLink can significantly reduce NAT Gateway and internet data transfer costs. Additionally, it lets you enforce stricter egress firewalls because none of the traffic to LaunchDarkly will traverse the public internet.
Prerequisites
Before you can configure PrivateLink, we'll need to add your AWS account to our allowlist. Contact your LaunchDarkly account manager or our Support team to get started.
The LaunchDarkly PrivateLink integration is available in the following AWS regions and availability zones:
us-east-1us-east-1d (use1-az1)us-east-1a (use1-az2)us-east-1e (use1-az3)us-east-1b (use1-az4)us-east-1f (use1-az5)us-east-1c (use1-az6)
Note that for other regions, you can use VPC Peering
Configure the LaunchDarkly integration in the AWS Console
This section describes how you use the AWS Console to configure the integration. You can also use Terraform or CloudFormation to configure the integration.
To configure the integration in the AWS Console:
- Go to the AWS VPC Console in the
us-east-1region. - Click on Endpoints in the left navigation pane.
- Click the Create Endpoint button in the top right. The Create Endpoint page appears.
- Enter your endpoint name, select "PrivateLink Ready partner services" as the category, enter
com.amazonaws.vpce.us-east-1.vpce-svc-02ce0367b7e976a75as the service name, and click Verify Service.
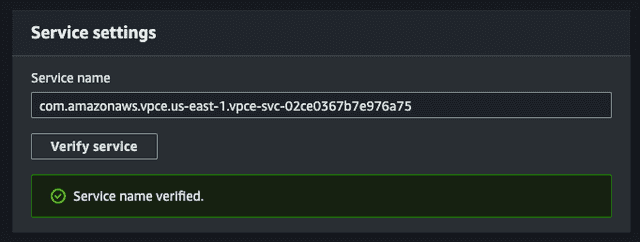
- Select the VPC to connect to the endpoint from.
- Select "Enable DNS Name" in Additional Settings. This enables
events.launchdarkly.comto resolve to this endpoint from within this VPC.
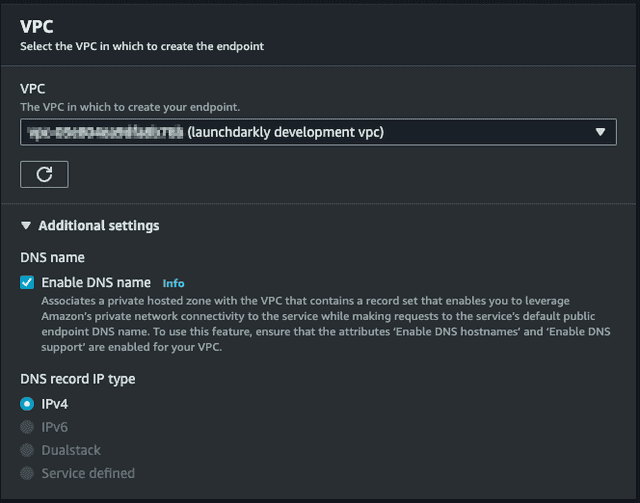
- Select subnets to use for the Availability Zones that you would like the endpoint to exist in.
- Select or create a Security Group that will allow inbound access on port
443from the VPC. - Click Create Endpoint. The endpoint enters a
Pendingstate. When the endpoint has been provisioned and becomesAvailable, traffic will begin to route through it.
To learn more, read Interface Endpoint Configuration and CloudWatch metrics for PrivateLink.