Splunk
Read time: 4 minutes
Last edited: Jul 12, 2024
The Splunk integration is available to customers on a Foundation or Enterprise plan. To learn more, read about our pricing. To upgrade your plan, contact Sales.
Overview
This topic explains how to use the LaunchDarkly Splunk integration. The Splunk integration exports LaunchDarkly audit events when a LaunchDarkly resource you care about, such as feature flags, projects, or account members, changes. You can use these events to create reports, charts, alerts and dashboards in Splunk.
Based on which type of Splunk account you have, endpoint hostnames, ports, and paths may differ from what's depicted in this topic. We indicate these differences when they occur in the text below.
Prerequisites
To configure the integration, you must have the following prerequisites:
- A Splunk HTTP Event Collector (HEC). To learn more, read Set up an HTTP Event Collector in Splunk Web
- An HEC token, which is generated during HEC setup.
Set up an HTTP Event Collector in Splunk Web
To add LaunchDarkly events to Splunk, you must configure and enable Splunk's HTTP Event Collector (HEC) in Splunk Web.
The steps to enable HEC vary based on your Splunk instance. To enable HEC, read Splunk's documentation.
Configure LaunchDarkly to work with Splunk
To configure LaunchDarkly to start sending events to Splunk:
- Navigate to the Integrations page and find "Splunk."
- Click Add integration. The "Create Splunk configuration" panel appears.
- (Optional) Give the integration a human-readable Name.
- Paste the HTTP event collector URL into the HTTP event collector base URL. This URL varies based on which version of Splunk you have. To learn more about which URL format to use, read Splunk's documentation.
- Paste your HEC token in the Token field.
- If you're using Splunk Cloud, you will probably need to check the Skip certificate verification checkbox. Splunk Cloud instances are deployed with self-signed SSL certificates which prevents LaunchDarkly's integration service from reaching Splunk Cloud's HEC service.
- (Optional) Configure a custom policy to control which event information LaunchDarkly sends to Splunk. To learn more about this option, read Add custom policies to the Splunk integration.
- After reading the Integration Terms and Conditions, check the I have read and agree to the Integration Terms and Conditions checkbox.
- Click Save configuration.
Splunk now receives events from LaunchDarkly.
If you want to further modify the events that Splunk receives from LaunchDarkly, add custom policies to determine which events the integration should export. If after following these steps, you still are not able to locate LaunchDarkly events, read the Troubleshooting section for further guidance.
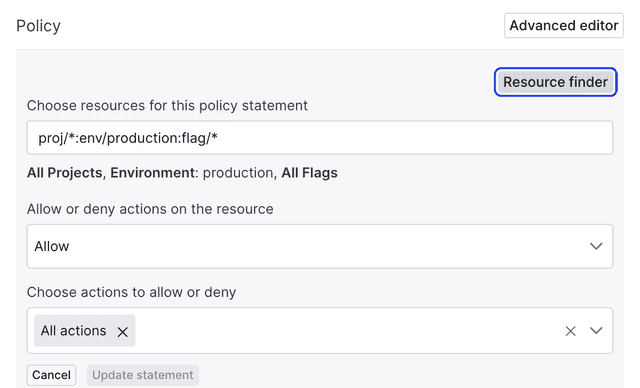
Add custom policies to the Splunk integration
By default, the Splunk integration sends production flag change events to Splunk. You can customize those events with the Policy editor, using the same language and construction as if you were creating a custom role.
To learn more, read Custom Roles.
You can customize the events LaunchDarkly sends to Splunk by using the policy editor in the Splunk configuration panel:
Access LaunchDarkly events in Splunk
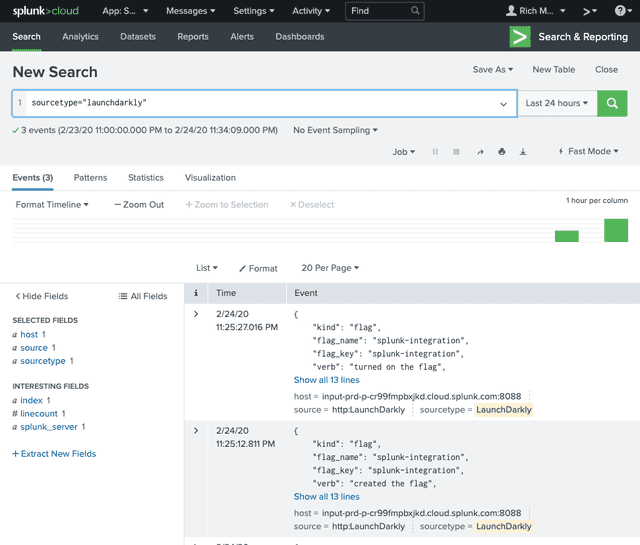
Now that your integration is configured, you can view LaunchDarkly events in Splunk.
Access those events with the following Splunk search query:
sourcetype="<NAME-OF-HTTP-EVENT-COLLECTOR>"
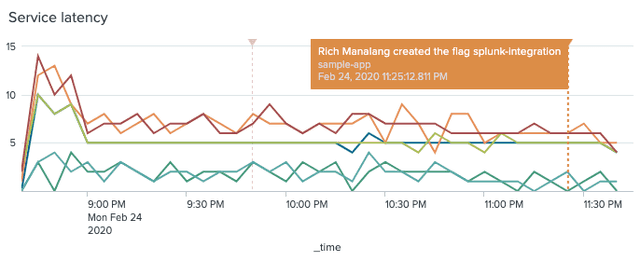
After LaunchDarkly events start appearing in Splunk, you can create event annotations in your charts in order to show LaunchDarkly events in context.
To learn more, read Splunk's documentation.
Troubleshooting
If you do not see LaunchDarkly events appearing in Splunk, confirm that incoming traffic is permitted. You can also recreate a single LaunchDarkly test event and verify that Splunk is receiving events.
Configure Splunk IP allow lists
Some Splunk customers may need to configure their Splunk IP allow lists to permit incoming traffic from LaunchDarkly. To do this, follow Splunk's Configure IP allow lists using Splunk Web documentation to configure the HEC access for ingestion allow list. Add the outboundAddresses from LaunchDarkly's Public IP list when configuring the IP allow list in Splunk.
Recreate the LaunchDarkly events collector in Splunk
If you configure the LaunchDarkly integration and events in Splunk do not appear, recreate the LaunchDarkly request with a curl.
Use this command to recreate the request:
curl -k \-X POST \-H "Authorization: Splunk <HTTP_EVENT_COLLECTOR_TOKEN>" \-d '{"event": "test"}' \https://<HTTP_EVENT_COLLECTOR_BASE_URL>/services/collector/event
- Splunk Enterprise URLs format:
<protocol>://<host>:<port>/<endpoint>. - Self-service Splunk Cloud URLs format:
<protocol>://input-<host>:<port>/<endpoint>. - Managed Splunk Cloud URLs format:
<protocol>://http-inputs-<host>:<port>/<endpoint>.
To learn more, read Splunk's documentation.
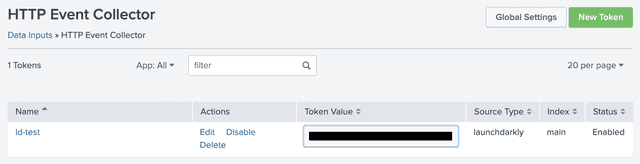
In Splunk, confirm that your HEC Global Settings and your specific HEC are set to 'Enabled' and that the Default Index type on your token is 'main'.
To search within Splunk for LaunchDarkly events using sourcetype="launchdarkly", set a custom sourcetype on your HEC token.
Set the Source Type as launchdarkly, set Index to main and set Status to Enabled.
An example token is below: