Creating private projects with custom roles
Read time: 3 minutes
Last edited: May 01, 2024
Overview
This topic explains how to use custom roles to create private projects or restrict access to projects. It gives examples of how to restrict access to one project, effectively creating a private project for members you choose, how to restrict access to all projects, and how to grant access only to one or some projects.
This topic uses the viewProject action to restrict and grant access to projects. To learn more about this action, read Using actions.
Viewing access is required to modify a resource, so if a member cannot view a resource, they also cannot modify it in any way. You can use the policies below to control who can access and modify the feature flags or other child resources in a project.
Restricting access to a project
This example policy forbids viewing access to a project called project-1.
This policy is useful for restricting access to a project to only those account members who are working on it.
The following code sample restricts view and edit access to a project:
[{"effect": "deny","actions": ["viewProject"],"resources": ["proj/project-1"]}]
Restricting access to all projects
This example policy forbids access to all projects. It is equivalent to the built-in No access role.
The following code sample restricts view and edit access to all projects:
[{"effect": "deny","actions": ["*"],"resources": ["*"]}]
Alternatively, to prevent members from viewing content in LaunchDarkly unless you give them access, you can uncheck the "By default, members can view all LaunchDarkly content" box when you create a custom role:
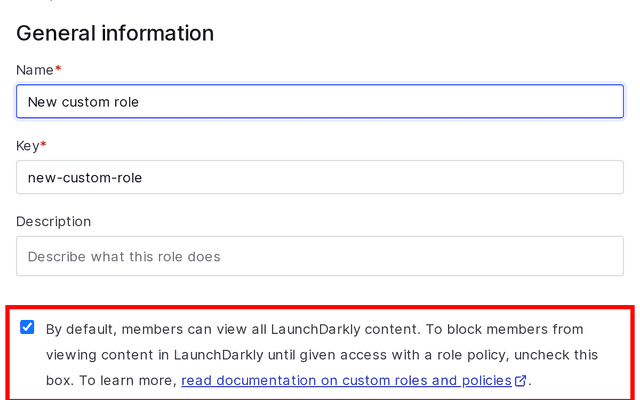
When this box is unchecked, you do not need to explicitly deny view access to projects because the custom role starts with no view or write access to anything in LaunchDarkly. Instead, you must explicitly allow view or write access to relevant projects and other LaunchDarkly resources.
Granting access to specific projects
You can restrict individual members' or teams' access to certain projects by explicitly denying view access to projects you do not want them to view. Excluding most projects effectively creates a flags list and project picker that only displays the projects you want a given member or group to view.
You can even restrict teams or members to their own project-based workspace by allowing them to view only one project.
The example below allows access to every project in an environment except the four listed in the resources parameter:
[{"effect": "deny","actions": ["viewProject"],"resources": ["proj/project-1","proj/project-2","proj/project-3","proj/project-4"]}]